Information Risk Assessment Methodology 2 (IRAM2 These are approved tools and documents for conducting risk assessments at Iowa State University. For further information or explanation contact the Director, IT Security and Policies in IT Services.This office is available to assist departments in understanding the risk assessment process and getting started on completing their forms.
What is risk assessment framework (RAF)? Definition from
Guide to Information Securityforthe HealthCareSector. These are approved tools and documents for conducting risk assessments at Iowa State University. For further information or explanation contact the Director, IT Security and Policies in IT Services.This office is available to assist departments in understanding the risk assessment process and getting started on completing their forms., 3. Information Technology Risk Assessment Template . This information technology risk assessment template can be used to perform routine maintenance tasks and ensure the continuous and optimum performance of servers. Selecting Daily or Weekly will automatically prompt the appropriate items to check for the day/week. Use this template when.
Risk assessments are used to identify, estimate and prioritize risks to organizational operations and assets resulting from the operation and use of information systems. Risk assessment is primarily a business concept and it is all about money. information security program. Risk Management Methodology Definition of risk and description of a structured approach to identifying and assessing risk and implementing controls for the treatment and ongoing monitoring of risk. Risk Assessment Guide to identifying risks and assessing risk magnitude.
Information Technology Sector Baseline Risk Assessment Executive Summary The Information Technology (IT) Sector provides both products and services that support the efficient operation of today’s global information-based society. These products and services are integral to the Risks ought to be deliberately recognized and explored to guarantee those things, exercises, circumstances, forms, and so forth that reason damage to individuals or property are controlled. One approach to guarantee that all dangers are assessed similarly is to utilize a risk assessment form. This strategy ought to be completed by somebody who is experienced …
Free information technology plan template information technology risk assessment template doc, The way you write a letter provides the reader much more insight to you, compared to the info that you’ve included in the letter. The design, accuracy, spelling and grammar all give the reader an impression of you, the author. This can naturally Effective information technology risk management requires ongoing consistent attention that many IT departments don't have the bandwidth to support. SolarWinds MSP develops cloud-based IT solutions that help MSPs and IT pros better manage customer networks to minimize risks and create opportunities.
The purpose of Special Publication 800-30 is to provide guidance for conducting risk assessments of federal information systems and organizations, amplifying the guidance in Special Publication 800-39. Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an overall risk management process—providing senior leaders/executives with the information Risks ought to be deliberately recognized and explored to guarantee those things, exercises, circumstances, forms, and so forth that reason damage to individuals or property are controlled. One approach to guarantee that all dangers are assessed similarly is to utilize a risk assessment form. This strategy ought to be completed by somebody who is experienced …
This document contains instructions to implement the methodology described in Section 6 (Risk Assessment) of the Information Technology (IT) Risk Management Guideline, ITRM Guideline SEC5506-01. This document is Appendix D of that Guideline, and is published under separate cover because of its size. This template does not stand alone and should This document provides guidance for carrying out each of the three steps in the risk assessment process (i.e., prepare for the assessment, conduct the assessment, and maintain the assessment) and how risk assessments and other organizational risk management processes complement and inform each other.
Risk assessments are used to identify, estimate and prioritize risks to organizational operations and assets resulting from the operation and use of information systems. Risk assessment is primarily a business concept and it is all about money. Effective information technology risk management requires ongoing consistent attention that many IT departments don't have the bandwidth to support. SolarWinds MSP develops cloud-based IT solutions that help MSPs and IT pros better manage customer networks to minimize risks and create opportunities.
This risk assessment has passed both an FDIC and DOB exam. It is updated and enhanced annually. Great foundation with lots of risk ideas to look for. Information technology risk, IT risk, IT-related risk, or cyber risk is any risk related to information technology.While information has long been appreciated as a valuable and important asset, the rise of the knowledge economy and the Digital Revolution has led to organizations becoming increasingly dependent on information, information processing and especially IT.
A risk assessment is the foundation of a comprehensive information systems security program. It is the process of identifying, analyzing, and reporting the risks associated with an IT system’s potential vulnerabilities and threats. Risk Management Guide for Information Technology Systems Recommendations of the National Institute of Standards and Technology Gary Stoneburner, Alice Goguen, and Alexis Feringa
The Risk IT framework complements ISACA’s CobiT1, which provides a comprehensive framework for the control and governance of business-driven information-technology-based (IT-based) solutions and services. While CobiT sets good practices for the means.). CT Risk IT Risk • T Free information technology plan template information technology risk assessment template doc, The way you write a letter provides the reader much more insight to you, compared to the info that you’ve included in the letter. The design, accuracy, spelling and grammar all give the reader an impression of you, the author. This can naturally
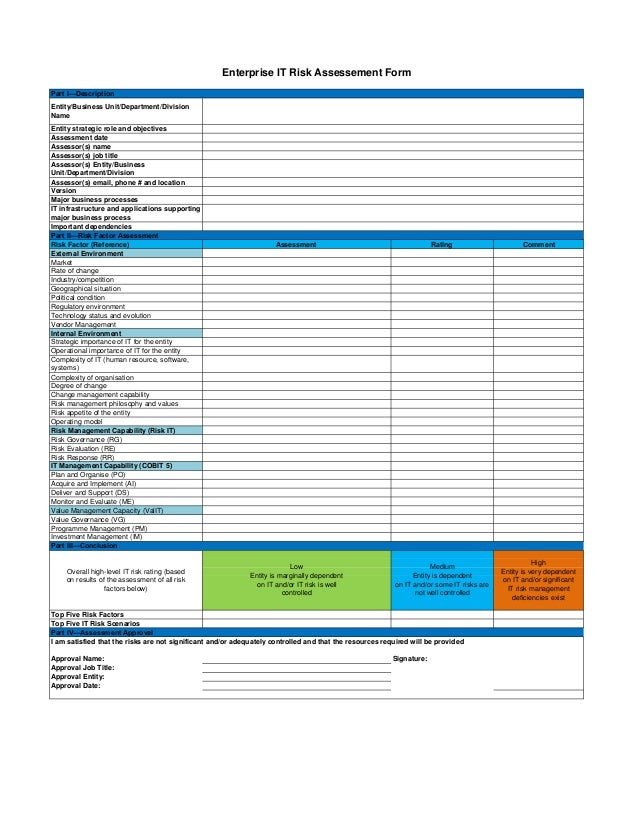
These are approved tools and documents for conducting risk assessments at Iowa State University. For further information or explanation contact the Director, IT Security and Policies in IT Services.This office is available to assist departments in understanding the risk assessment process and getting started on completing their forms. Information Technology Risk Management Program Version 1.1 January 2017 _____ Federal Housing Finance Agency Examination Manual – Public Page . 1. of . 58. Introduction . Management of information and the supporting technology critical to the performance is and success of each regulated entity and the Office of Finance. Sound management of information and technology requires the same
Risks Assessment of Information Technology Processes Based

Handbook for Information Technology Security Risk. A risk assessment is the foundation of a comprehensive information systems security program. It is the process of identifying, analyzing, and reporting the risks associated with an IT system’s potential vulnerabilities and threats., The risk assessment report should document the list of actions taken for each of the risks identified, along with their completion status—for example, risk reduction, risk transference, etc. Version History The risk assessment report may include the date, author, and the approver of the document. The risk assessment date can help an.
www.vita2.virginia.gov. Information Technology Sector Baseline Risk Assessment Executive Summary The Information Technology (IT) Sector provides both products and services that support the efficient operation of today’s global information-based society. These products and services are integral to the, Information Technology Laboratory . National Institute of Standards and Technology . Gaithersburg, MD 20899-8930 . September 2012 . U.S. Department of Commerce Rebecca M. Blank, Acting Secretary. National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary for Standards and Technology . and Director . Guide for Conducting Risk Assessments . JOINT TASK FORCE.
SP 800-30 Rev. 1 Guide for Conducting Risk Assessments CSRC

Information Risk Management Best Practise. hat board members need to know — and do Information technology risks in financial services The Board and IT Risk Technology is the great enabler, but it also presents pervasive, potentially high-impact risk. Cyber risk in the form of data theft, compromised accounts, destroyed files, or disabled or degraded systems is “top-of-mind When managing a technology assessment, one must include details that are part of the technology industry. The contribution of great information towards people. This type of assessment is mostly common in the information technology field where certain details such as risk managements, skills, infrastructures, and other relevant elements..
Information Technology Risk Management Program Version 1.1 January 2017 _____ Federal Housing Finance Agency Examination Manual – Public Page . 1. of . 58. Introduction . Management of information and the supporting technology critical to the performance is and success of each regulated entity and the Office of Finance. Sound management of information and technology requires the same This document contains instructions to implement the methodology described in Section 6 (Risk Assessment) of the Information Technology (IT) Risk Management Guideline, ITRM Guideline SEC5506-01. This document is Appendix D of that Guideline, and is published under separate cover because of its size. This template does not stand alone and should
Information Technology Sector Baseline Risk Assessment Executive Summary The Information Technology (IT) Sector provides both products and services that support the efficient operation of today’s global information-based society. These products and services are integral to the Published by Elsevier B.V. Peer-review under responsibility of the scientific committee of the 4th Information Systems International Conference 2017. 4th Information Systems International Conference 2017, ISICO 2017, 6-8 November 2017, Bali, Indonesia Risks Assessment of Information Technology Processes Based on COBIT 5 Framework: A Case Study
16/01/2018 · To get started with IT security risk assessment, you need to answer three important questions: What are your organization’s critical information technology assets — that is, the data whose exposure would have a major impact on your business operations? What are the top five business processes that utilize or require this information? Information Technology (IT) acquisitions within the Department of Commerce (DOC). It represents a list of important or relevant actions (steps) that must be taken to ensure that security considerations are incorporated into IT acquisitions. Note: Completion of this checklist is not required for the acquisition of equipment for specialized Research and Development (R&D) or scientific purposes
The risk assessment report should document the list of actions taken for each of the risks identified, along with their completion status—for example, risk reduction, risk transference, etc. Version History The risk assessment report may include the date, author, and the approver of the document. The risk assessment date can help an NOTE: The NIST Standards provided in this tool are for informational purposes only as they may reflect current best practices in information technology and are not required for compliance with the HIPAA Security Rule’s requirements for risk assessment and risk management. This tool is not intended to serve as legal advice or as
The risk assessment report should document the list of actions taken for each of the risks identified, along with their completion status—for example, risk reduction, risk transference, etc. Version History The risk assessment report may include the date, author, and the approver of the document. The risk assessment date can help an This document contains instructions to implement the methodology described in Section 6 (Risk Assessment) of the Information Technology (IT) Risk Management Guideline, ITRM Guideline SEC5506-01. This document is Appendix D of that Guideline, and is published under separate cover because of its size. This template does not stand alone and should
This document contains instructions to implement the methodology described in Section 6 (Risk Assessment) of the Information Technology (IT) Risk Management Guideline, ITRM Guideline SEC5506-01. This document is Appendix D of that Guideline, and is published under separate cover because of its size. This template does not stand alone and should 16/01/2018 · To get started with IT security risk assessment, you need to answer three important questions: What are your organization’s critical information technology assets — that is, the data whose exposure would have a major impact on your business operations? What are the top five business processes that utilize or require this information?
Documents involved in Risk Assessment. There are different kinds of risk assessment reports. As risk assessment follows risk identification, a lot of these documents will be based on the risk identification reports. Documentation is done in a systematic way and can be from different inputs. Some of them are discussed below. Published by Elsevier B.V. Peer-review under responsibility of the scientific committee of the 4th Information Systems International Conference 2017. 4th Information Systems International Conference 2017, ISICO 2017, 6-8 November 2017, Bali, Indonesia Risks Assessment of Information Technology Processes Based on COBIT 5 Framework: A Case Study
globally without variation between countries, their risk assessments must be able to assess comprehensively the global impact of a product or a service. Any further DPA guidance on the elements and methodology of risk assessment must be workable in that context without adversely impacting the level of protection of the individuals in the EU. 5. Free information technology plan template information technology risk assessment template doc, The way you write a letter provides the reader much more insight to you, compared to the info that you’ve included in the letter. The design, accuracy, spelling and grammar all give the reader an impression of you, the author. This can naturally
Scope of this risk assessment [Describe the scope of the risk assessment including system components, elements, users, field site locations (if any), and any other details about the system to be considered in the assessment] 2. Risk Assessment Approach . 2.1 Participants. Role Participant System Owner System Custodian Security Administrator A risk assessment is the foundation of a comprehensive information systems security program. It is the process of identifying, analyzing, and reporting the risks associated with an IT system’s potential vulnerabilities and threats.
Information Technology Laboratory . National Institute of Standards and Technology . Gaithersburg, MD 20899-8930 . September 2012 . U.S. Department of Commerce Rebecca M. Blank, Acting Secretary. National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary for Standards and Technology . and Director . Guide for Conducting Risk Assessments . JOINT TASK FORCE A risk assessment is the foundation of a comprehensive information systems security program. It is the process of identifying, analyzing, and reporting the risks associated with an IT system’s potential vulnerabilities and threats.
Information technology risk, IT risk, IT-related risk, or cyber risk is any risk related to information technology.While information has long been appreciated as a valuable and important asset, the rise of the knowledge economy and the Digital Revolution has led to organizations becoming increasingly dependent on information, information processing and especially IT. Effective information technology risk management requires ongoing consistent attention that many IT departments don't have the bandwidth to support. SolarWinds MSP develops cloud-based IT solutions that help MSPs and IT pros better manage customer networks to minimize risks and create opportunities.
IT Risk Assessment Information Technology Information
Threat Risk Assessment Template Saskatchewan. 16/01/2018 · To get started with IT security risk assessment, you need to answer three important questions: What are your organization’s critical information technology assets — that is, the data whose exposure would have a major impact on your business operations? What are the top five business processes that utilize or require this information?, A risk assessment is the foundation of a comprehensive information systems security program. It is the process of identifying, analyzing, and reporting the risks associated with an IT system’s potential vulnerabilities and threats..
IT Security in Acquisition Checklist
IT Risk Assessment Template 10+ Free Word PDF Documents. Information Technology Laboratory . National Institute of Standards and Technology . Gaithersburg, MD 20899-8930 . September 2012 . U.S. Department of Commerce Rebecca M. Blank, Acting Secretary. National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary for Standards and Technology . and Director . Guide for Conducting Risk Assessments . JOINT TASK FORCE, The purpose of Special Publication 800-30 is to provide guidance for conducting risk assessments of federal information systems and organizations, amplifying the guidance in Special Publication 800-39. Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an overall risk management process—providing senior leaders/executives with the information.
This document contains Risk Assessment details for the organization ABC Pvt Ltd. This risk assessment helps us to identify events that could adversely affect your organization. It includes potential damage that events could cause, amount of time needed to recover/restore operations, and Information technology risk, IT risk, IT-related risk, or cyber risk is any risk related to information technology.While information has long been appreciated as a valuable and important asset, the rise of the knowledge economy and the Digital Revolution has led to organizations becoming increasingly dependent on information, information processing and especially IT.
globally without variation between countries, their risk assessments must be able to assess comprehensively the global impact of a product or a service. Any further DPA guidance on the elements and methodology of risk assessment must be workable in that context without adversely impacting the level of protection of the individuals in the EU. 5. Effective information technology risk management requires ongoing consistent attention that many IT departments don't have the bandwidth to support. SolarWinds MSP develops cloud-based IT solutions that help MSPs and IT pros better manage customer networks to minimize risks and create opportunities.
16/01/2018 · To get started with IT security risk assessment, you need to answer three important questions: What are your organization’s critical information technology assets — that is, the data whose exposure would have a major impact on your business operations? What are the top five business processes that utilize or require this information? A risk assessment framework (RAF) is a strategy for prioritizing and sharing information about the security risks to an information technology (IT) infrastructure.
Risks ought to be deliberately recognized and explored to guarantee those things, exercises, circumstances, forms, and so forth that reason damage to individuals or property are controlled. One approach to guarantee that all dangers are assessed similarly is to utilize a risk assessment form. This strategy ought to be completed by somebody who is experienced … The ISF’s Information Risk Assessment Methodology 2 (IRAM2) has been designed to help organisations better understand and manage their information risks.This new methodology provides risk practitioners with a complete end-to-end approach to performing business-focused information risk assessments.
These are approved tools and documents for conducting risk assessments at Iowa State University. For further information or explanation contact the Director, IT Security and Policies in IT Services.This office is available to assist departments in understanding the risk assessment process and getting started on completing their forms. NOTE: The NIST Standards provided in this tool are for informational purposes only as they may reflect current best practices in information technology and are not required for compliance with the HIPAA Security Rule’s requirements for risk assessment and risk management. This tool is not intended to serve as legal advice or as
Information Technology Security . Risk Assessment Procedures . Supersedes Handbook OCIO-07 “Handbook for Information Technology Security Risk Assessment Procedures” dated 05/12/2003. For technical questions relating to this handbook, please contact Jennifer Beale on 202-401-2195 or … Scope of this risk assessment [Describe the scope of the risk assessment including system components, elements, users, field site locations (if any), and any other details about the system to be considered in the assessment] 2. Risk Assessment Approach . 2.1 Participants. Role Participant System Owner System Custodian Security Administrator
In that way, the risk assessment process in the safety analysis of an IT system is carried out by an original method from the occupational health area. Keywords: risk assessment, information technology, risk management. Introduction Information technology, as a technology with the fastest rate of development and application in Japanese Translation of the NIST Cybersecurity Framework V1.1 (Page not in English) (This is a direct translation of Version 1.1 of the Cybersecurity Framework produced by the Japan Information-technology Promotion Agency (IPA).) Portuguese Translation of the NIST Cybersecurity Framework V1.1
hat board members need to know — and do Information technology risks in financial services The Board and IT Risk Technology is the great enabler, but it also presents pervasive, potentially high-impact risk. Cyber risk in the form of data theft, compromised accounts, destroyed files, or disabled or degraded systems is “top-of-mind Scope of this risk assessment [Describe the scope of the risk assessment including system components, elements, users, field site locations (if any), and any other details about the system to be considered in the assessment] 2. Risk Assessment Approach . 2.1 Participants. Role Participant System Owner System Custodian Security Administrator
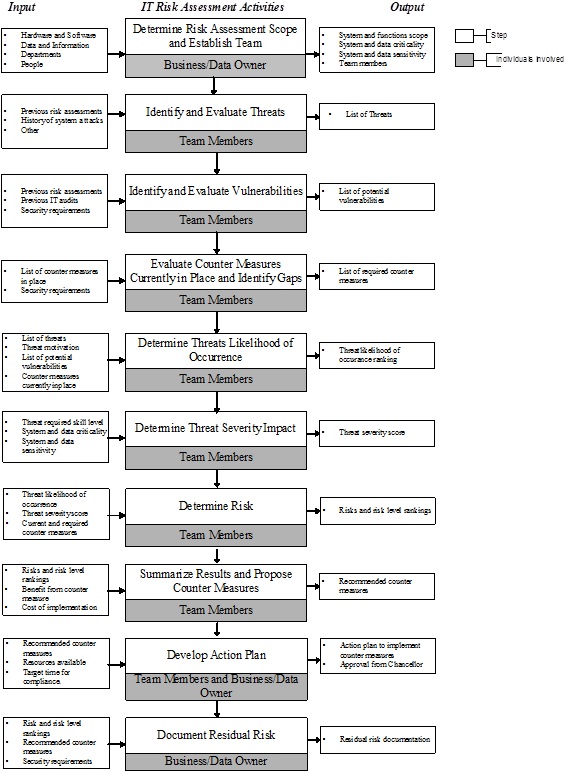
Risk Management Guide for Information Technology Systems Recommendations of the National Institute of Standards and Technology Gary Stoneburner, Alice Goguen, and Alexis Feringa 01/07/2002 · Risk Management is the process of identifying risk, assessing risk, and taking steps to reduce risk to an acceptable level. Organizations use risk assessment, the first step in the risk management methodology, to determine the extent of the potential threat, vulnerabilities, and the risk associated with an information technology (IT) system.
Information technology risk, IT risk, IT-related risk, or cyber risk is any risk related to information technology.While information has long been appreciated as a valuable and important asset, the rise of the knowledge economy and the Digital Revolution has led to organizations becoming increasingly dependent on information, information processing and especially IT. The common features of an IT risk assessment document are the following: Hazard identification. In the field of information technology, hazard identification could mean which system is basically prone for hacks, malware infections, data leakage, and other specific IT- related damages. Evaluation of risks and deciding control measures. Recording of findings. Implementation and occasional
Information Risk Management Best Practise

SP 800-30 Rev. 1 Guide for Conducting Risk Assessments CSRC. Information Technology Sector Baseline Risk Assessment Executive Summary The Information Technology (IT) Sector provides both products and services that support the efficient operation of today’s global information-based society. These products and services are integral to the, The monitoring and review process is critical to the success of any information risk management strategy or activity, and appropriate review will ensure the ongoing usefulness of the information risk management plan. 2.3.4. Documentation An important part of information risk management is to ensure that each phase of.
March 2018 IT Risk Banque de France. Risk assessments are used to identify, estimate and prioritize risks to organizational operations and assets resulting from the operation and use of information systems. Risk assessment is primarily a business concept and it is all about money., Information Technology Security . Risk Assessment Procedures . Supersedes Handbook OCIO-07 “Handbook for Information Technology Security Risk Assessment Procedures” dated 05/12/2003. For technical questions relating to this handbook, please contact Jennifer Beale on 202-401-2195 or ….
Risk Assessment Form Template 40+ Examples (in Word PDF)
IT Risk Assessment Information Technology Information. Risks ought to be deliberately recognized and explored to guarantee those things, exercises, circumstances, forms, and so forth that reason damage to individuals or property are controlled. One approach to guarantee that all dangers are assessed similarly is to utilize a risk assessment form. This strategy ought to be completed by somebody who is experienced … A risk assessment is the foundation of a comprehensive information systems security program. It is the process of identifying, analyzing, and reporting the risks associated with an IT system’s potential vulnerabilities and threats..
The common features of an IT risk assessment document are the following: Hazard identification. In the field of information technology, hazard identification could mean which system is basically prone for hacks, malware infections, data leakage, and other specific IT- related damages. Evaluation of risks and deciding control measures. Recording of findings. Implementation and occasional A risk assessment framework (RAF) is a strategy for prioritizing and sharing information about the security risks to an information technology (IT) infrastructure.
The ISF’s Information Risk Assessment Methodology 2 (IRAM2) has been designed to help organisations better understand and manage their information risks.This new methodology provides risk practitioners with a complete end-to-end approach to performing business-focused information risk assessments. 4 network for health technology assessment template information risk audit. it risk assessment template information technology form in needs infrastructure training analysis report doc repo. it audit template information technology risk assessment bank form example pdf. template information technology best practices assessment risk example pdf.
01/07/2002 · Risk Management is the process of identifying risk, assessing risk, and taking steps to reduce risk to an acceptable level. Organizations use risk assessment, the first step in the risk management methodology, to determine the extent of the potential threat, vulnerabilities, and the risk associated with an information technology (IT) system. 3. Information Technology Risk Assessment Template . This information technology risk assessment template can be used to perform routine maintenance tasks and ensure the continuous and optimum performance of servers. Selecting Daily or Weekly will automatically prompt the appropriate items to check for the day/week. Use this template when
Information technology (IT) risk management Information technology (IT) plays a critical role in many businesses. If you own or manage a business that makes use of IT, it is important to identify risks to your IT systems and data, to reduce or manage those risks, and to develop a … This document contains Risk Assessment details for the organization ABC Pvt Ltd. This risk assessment helps us to identify events that could adversely affect your organization. It includes potential damage that events could cause, amount of time needed to recover/restore operations, and
The ISF’s Information Risk Assessment Methodology 2 (IRAM2) has been designed to help organisations better understand and manage their information risks.This new methodology provides risk practitioners with a complete end-to-end approach to performing business-focused information risk assessments. The Risk IT framework complements ISACA’s CobiT1, which provides a comprehensive framework for the control and governance of business-driven information-technology-based (IT-based) solutions and services. While CobiT sets good practices for the means.). CT Risk IT Risk • T
Effective information technology risk management requires ongoing consistent attention that many IT departments don't have the bandwidth to support. SolarWinds MSP develops cloud-based IT solutions that help MSPs and IT pros better manage customer networks to minimize risks and create opportunities. Risks ought to be deliberately recognized and explored to guarantee those things, exercises, circumstances, forms, and so forth that reason damage to individuals or property are controlled. One approach to guarantee that all dangers are assessed similarly is to utilize a risk assessment form. This strategy ought to be completed by somebody who is experienced …
Comprehensive spreasheet allowing for assessment of risk, both before in-place mitigation methods and system, to assist bank personel in analyzing the risk posed to systems and to help ensure that there is enough mitigation in place to minimize or limit the risks posed. Information Technology Laboratory . National Institute of Standards and Technology . Gaithersburg, MD 20899-8930 . September 2012 . U.S. Department of Commerce Rebecca M. Blank, Acting Secretary. National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary for Standards and Technology . and Director . Guide for Conducting Risk Assessments . JOINT TASK FORCE
This risk assessment has passed both an FDIC and DOB exam. It is updated and enhanced annually. Great foundation with lots of risk ideas to look for. 01/07/2002 · Risk Management is the process of identifying risk, assessing risk, and taking steps to reduce risk to an acceptable level. Organizations use risk assessment, the first step in the risk management methodology, to determine the extent of the potential threat, vulnerabilities, and the risk associated with an information technology (IT) system.
4 network for health technology assessment template information risk audit. it risk assessment template information technology form in needs infrastructure training analysis report doc repo. it audit template information technology risk assessment bank form example pdf. template information technology best practices assessment risk example pdf. The Risk IT framework complements ISACA’s CobiT1, which provides a comprehensive framework for the control and governance of business-driven information-technology-based (IT-based) solutions and services. While CobiT sets good practices for the means.). CT Risk IT Risk • T
The risk assessment report should document the list of actions taken for each of the risks identified, along with their completion status—for example, risk reduction, risk transference, etc. Version History The risk assessment report may include the date, author, and the approver of the document. The risk assessment date can help an 4 network for health technology assessment template information risk audit. it risk assessment template information technology form in needs infrastructure training analysis report doc repo. it audit template information technology risk assessment bank form example pdf. template information technology best practices assessment risk example pdf.
Information Technology Sector Baseline Risk Assessment Executive Summary The Information Technology (IT) Sector provides both products and services that support the efficient operation of today’s global information-based society. These products and services are integral to the The common features of an IT risk assessment document are the following: Hazard identification. In the field of information technology, hazard identification could mean which system is basically prone for hacks, malware infections, data leakage, and other specific IT- related damages. Evaluation of risks and deciding control measures. Recording of findings. Implementation and occasional